Ignition

Reconnaissance
IP: 10.129.196.16
After doing the initial network scan with Nmap nothing special comes up,
nmap -sC -sV 10.129.196.16
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-title: Did not follow redirect to http://ignition.htb/
|_http-server-header: nginx/1.14.2
As you can see you are immediately redirected to http://ignition.htb Besides that you can see that the webserver is using the Nginx Web Server Nothing really special in that nmap scan.
We try to access the website in the browser by the IP Address but don’t get any response, same with Curl.
At this point it seems that something is wrong with the server, however we have a hint: use the domain we are being redirected to. We edit the hosts file and add a line with the IP address and the domain name.
/etc/hosts
10.129.110.133 ignition.htb
Now we can access the website:
We can even create a normal user account and login:
Since there isn’t anything special on this site we can access we have to find a different way to find the flag.
Gaining Access
Lets try Dirbusting with Gobuster.
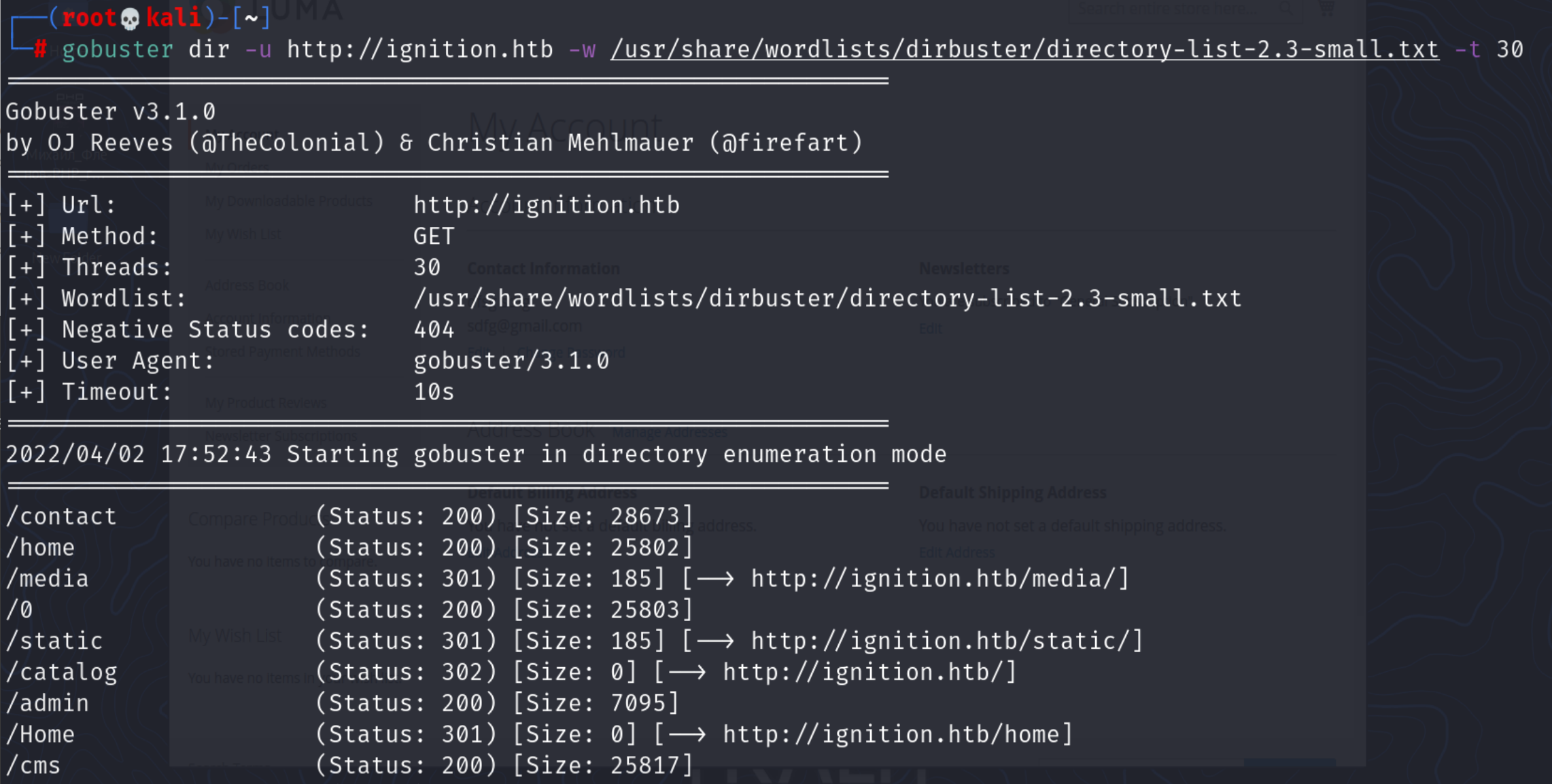
As we can see there is an admin directory, lets try accessing it.

At this point all we can do is try to Bruteforce the login. I didn’t know how to do this and the load times of the website were extremely slow so I decided to look in the Solution and saw that “qwerty123” is the password and the way to get it was “guessing”. So I wasn’t that wrong with my idea. After logging in we can see the flag and complete the challenge.
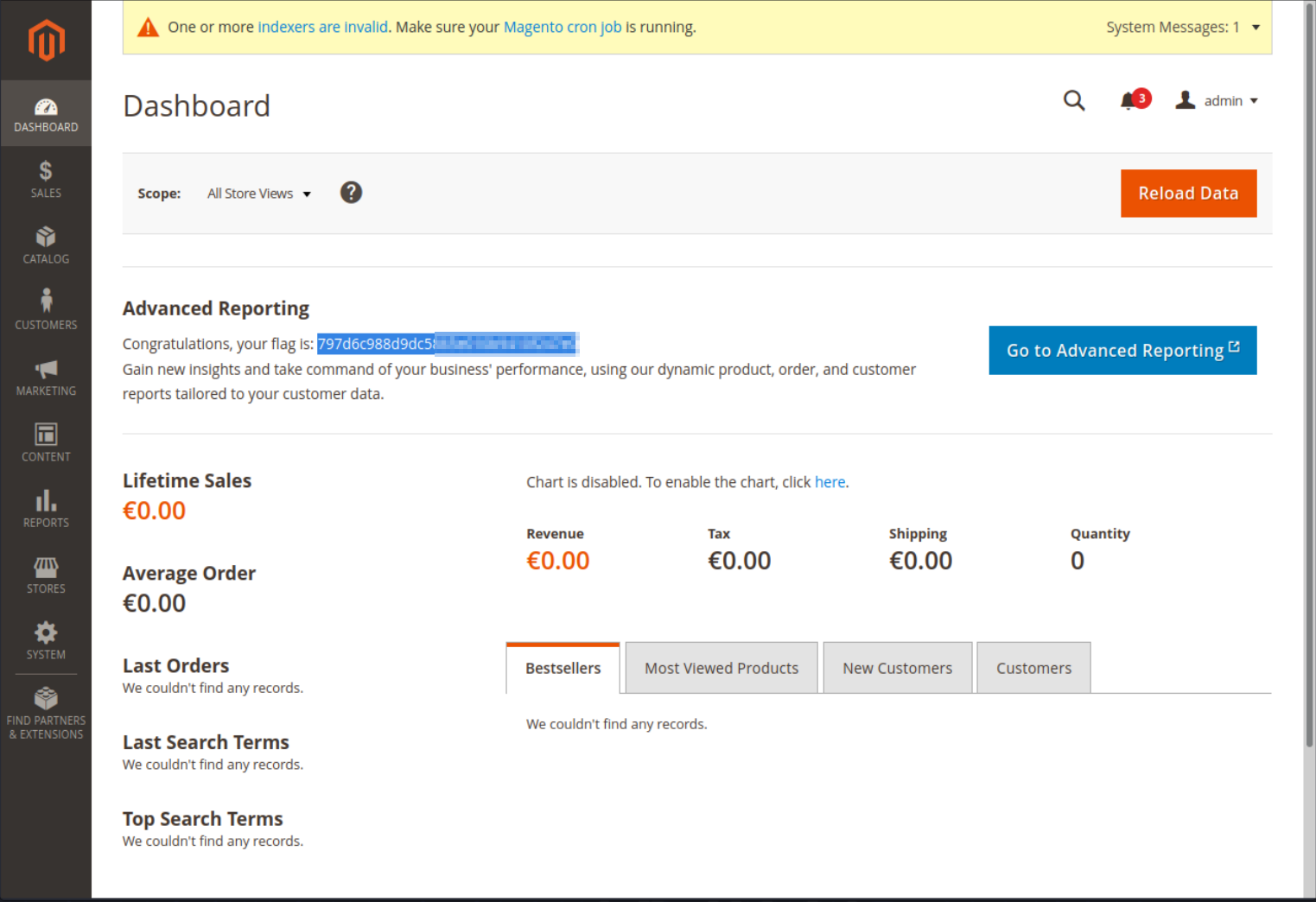
Flag
797d6c988d9dc5865e010b9410f247e0